Global Cyber Attacks
By identifying global cyber attack trends in advance, you can prepare countermeasures before they reach our country, and establish customized defense strategies by pre-checking risk levels of overseas branches or partner companies.
For global business enterprises, you can pre-evaluate the cybersecurity environment of target countries and reflect security risks in business plans.
Global Cyber Attacks
Domain Leak Management
Summary Report
Leak Details
Response History
Subdomain Exploration
Docs / Email Leak Detection
Completed
Pending
Inquiry

Key Features
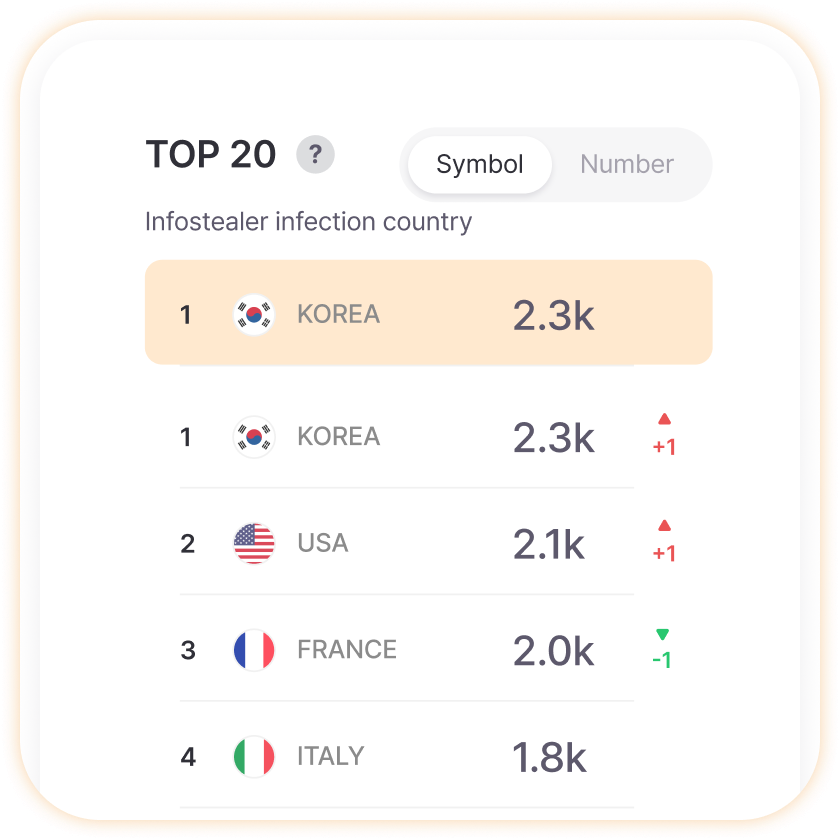
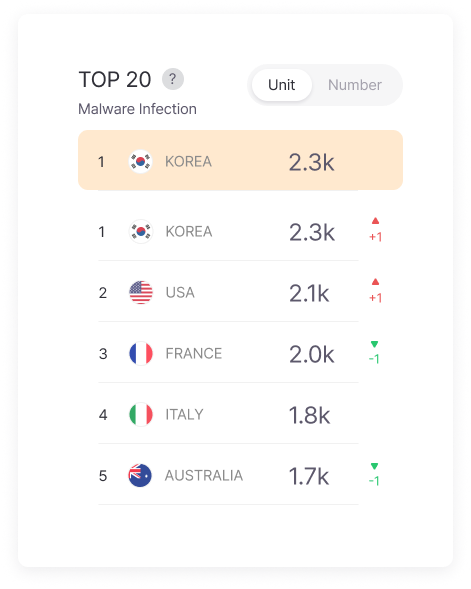
Top 20 Infostealer-Infected Countries
Know in advance which countries are more dangerous when our company works with overseas branches or partners to prepare additional security measures. Strengthen security checks for users accessing from specific countries or more thoroughly configure security settings for devices used during overseas business trips to effectively manage security risks in global business environments.

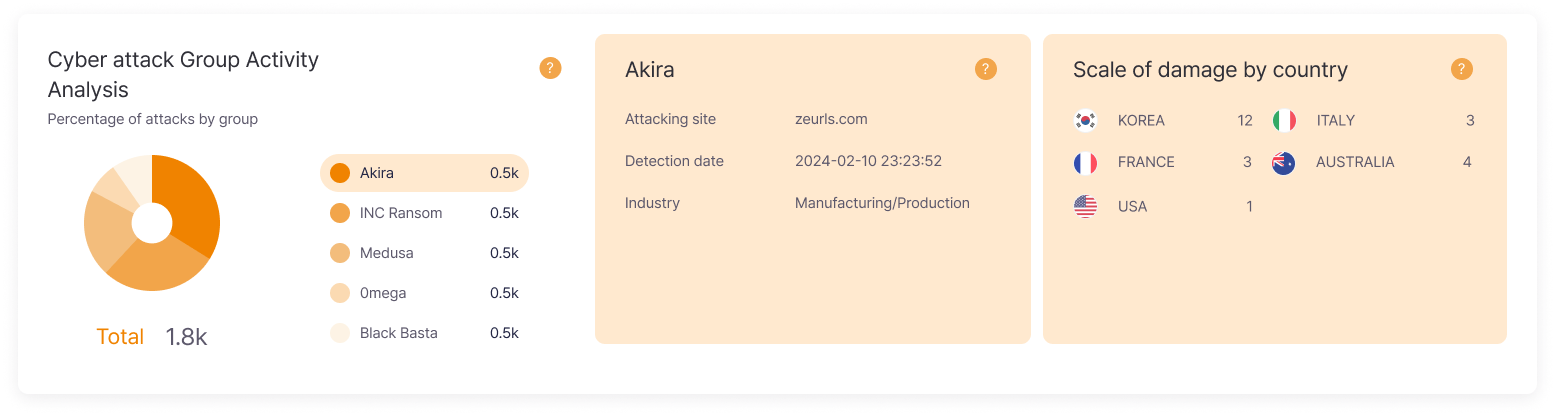
Attack Proportion by Group
Know which hacker groups are most actively operating to prepare defense strategies suited to those groups’ attack methods in advance. For example, if a specific group mainly conducts email attacks, strengthen email security, and if another group frequently hacks websites, invest more in web security to establish efficient security investment plans.

Group Attack Status
Know what attacks other companies in the same industry are receiving to prepare in advance thinking ‘we could receive similar attacks.’ Real-time identification of what new attack methods are emerging allows securing competitive advantage by proactively preparing security patches or countermeasures before they become known through news or reports.
Damage Scale by Country
If planning global expansion, judge which countries are safer in terms of cyber security to help establish business expansion strategies. Also understand our country’s relative risk level by identifying worldwide cyber attack trends, and use as evidence to objectively evaluate national-level security policy changes or international cooperation needs.




