Dark Web Leak Information Dashboard
ZeroDarkWeb
Accurately categorize the levels of information leaks on the dark web,
and comprehensively understand the status of leaked email accounts and malware infections.
Request a Demo for ZeroDarkWeb
"
"
"
"
Summary
Global Cyber Attacks
Domain Leak Report
Management
Leaked account
Response History

Domain Leak Report
The Domain Leak Report enables companies to swiftly evaluate their security posture and strategically plan their responses. It classifies information leakage levels on the dark web into ‘Critical’, ‘Caution’, and ‘Safe’, and documents these findings.Additionally, the report offers an in-depth analysis of email account and email attachment leak status. It also oversees the leakage status and security of information tied to critical keywords for the company, delivering detailed IP-based malware infection reports to holistically assist companies in addressing cyber threats.
Summary
Global Cyber Attacks
Domain Leak Report
Management
Leaked account
Response History

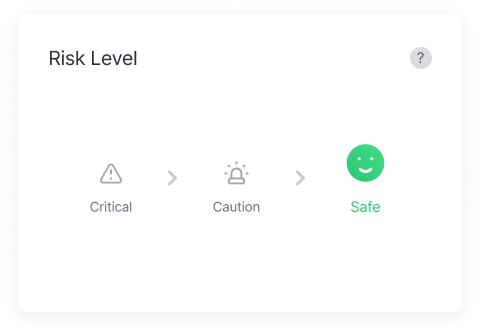
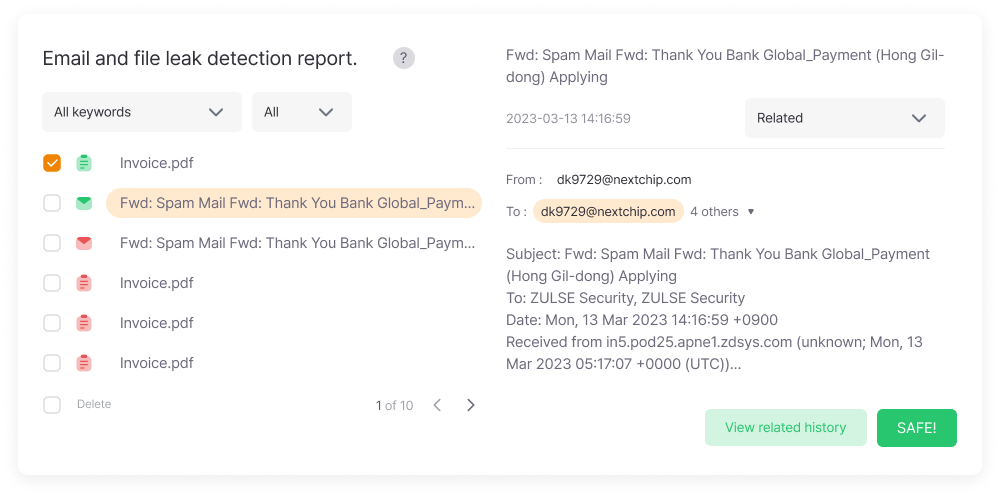

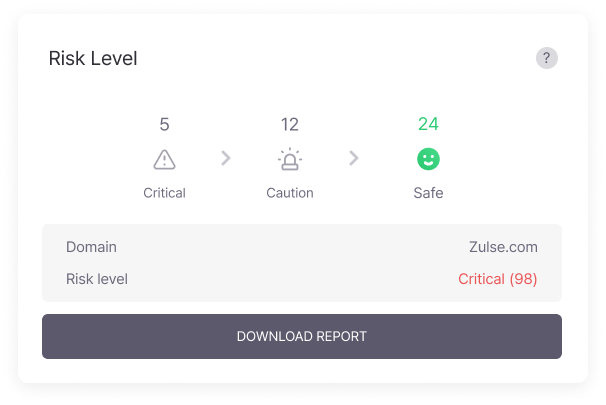
Dark Web Information Leakage Levels
Classifies the severity of information leaks on the dark web into ‘Critical‘, ‘Caution’, and ‘Safe’, allowing users to quickly assess their security status and take appropriate actions.

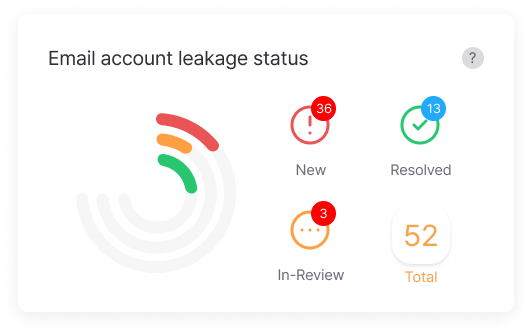
Email Account Leakage Status
Analyzes and reports the status of email account leaks, categorizing them into new leaks, in-review, resolved, and total leaks, enabling users to accurately understand their response status.

Email Attachment Leak Detection
Provides information on the status of email attachment leaks and detects potential data leaks, supporting the management of data leakage risks through email attachments. Monitors and manages the leakage status and safety of information related to specific keywords, ensuring systematic tracking of critical information security.

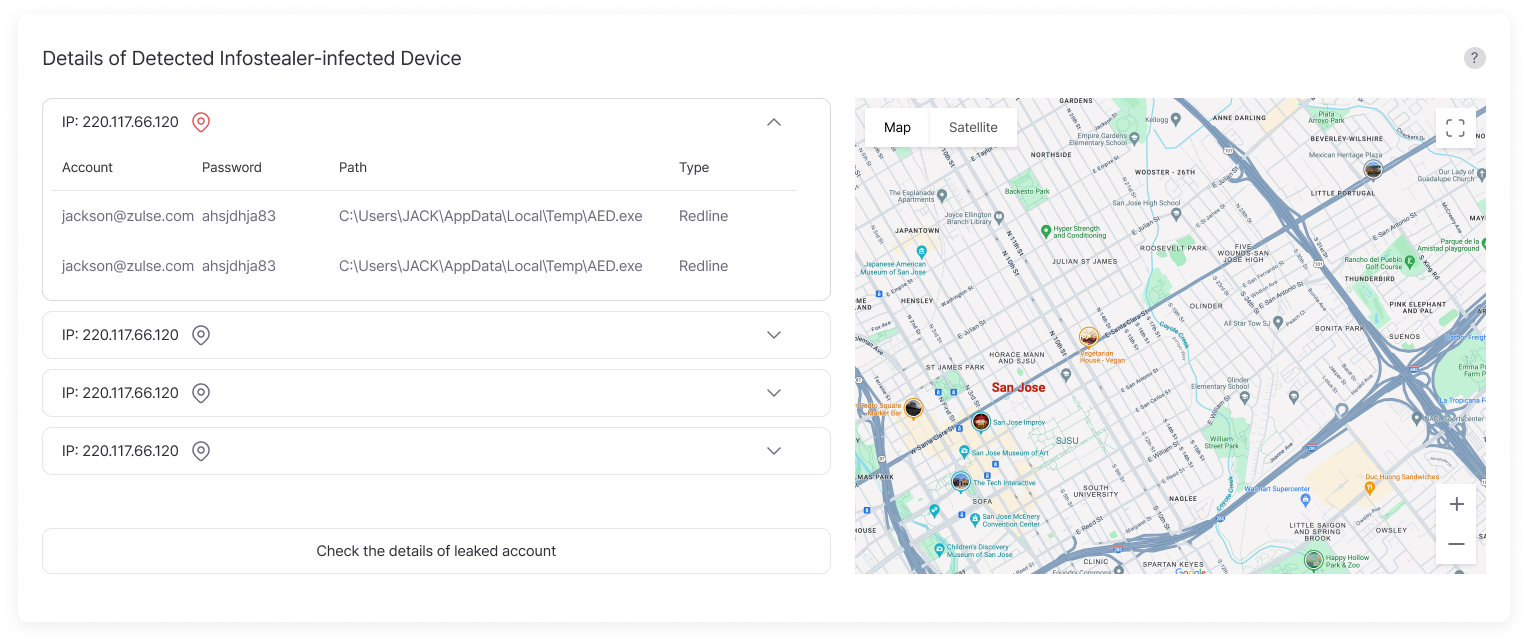
Detailed Malware Infection Report
Provides detailed IP-based reports on malware infections, including IDs, passwords, file paths, and types of malware, allowing companies to develop proactive response and resolution strategies.
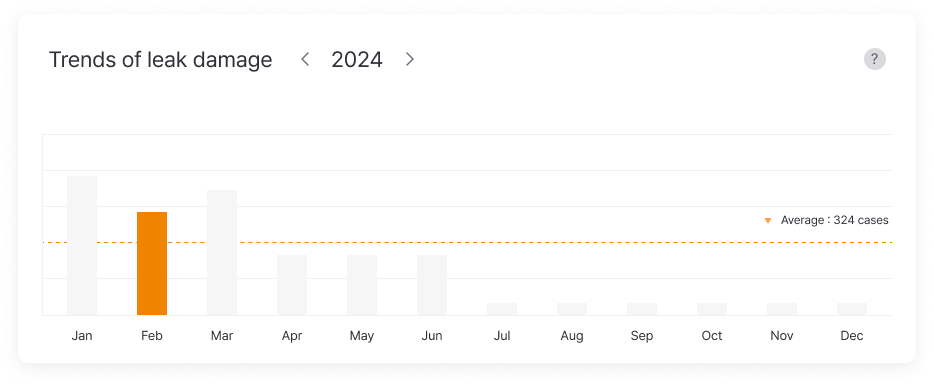
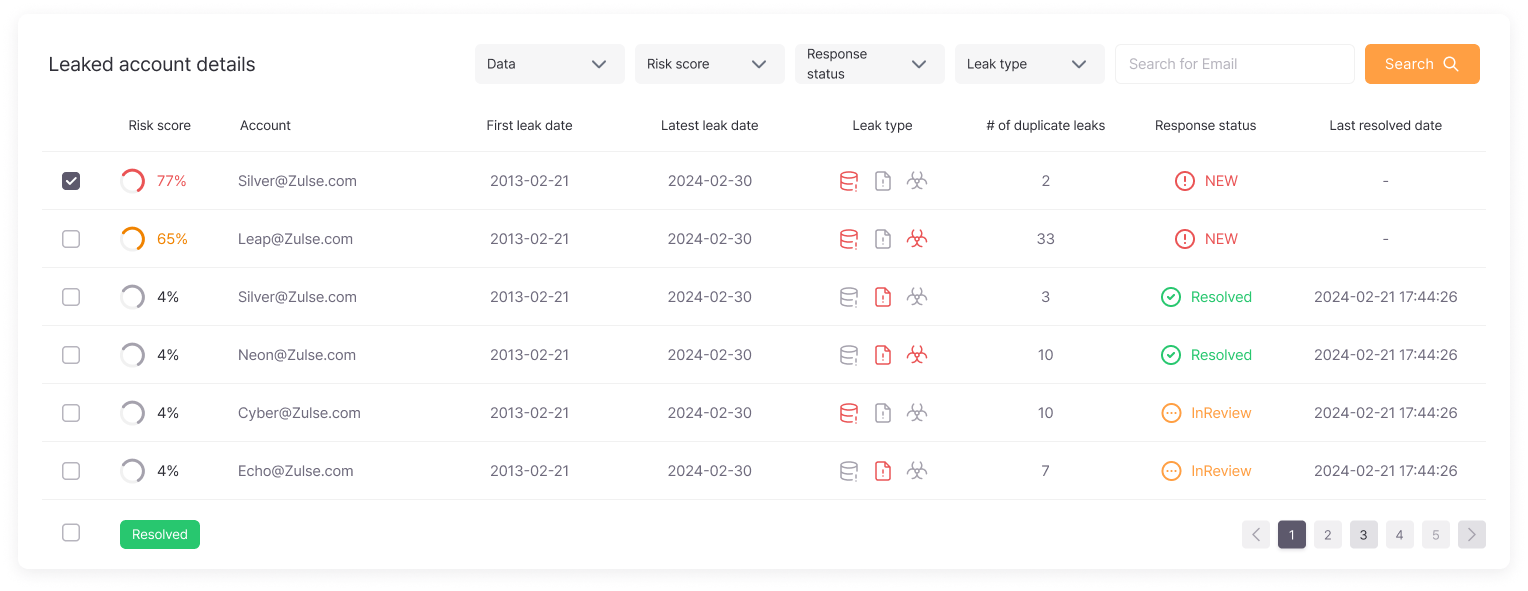
Detailed Information on Leaks
The detailed leak feature allows companies to gain comprehensive insights into their information leak incidents. It categorizes leak levels into critical, caution, and safe, and presents the response status by period and type. Trends in leak response and damage fluctuations are displayed as graphs. Leaked account information is presented in a list view, enabling companies to quickly locate necessary details using filtering and search functions. The detailed view offers extensive information, including risk score, ID, and leak type. Additionally, it provides recommended response actions and leak history, aiding companies in effectively managing their information leakage situations.
Summary
Global Cyber Attacks
Domain Leak Report
Management
Leaked account
Response History







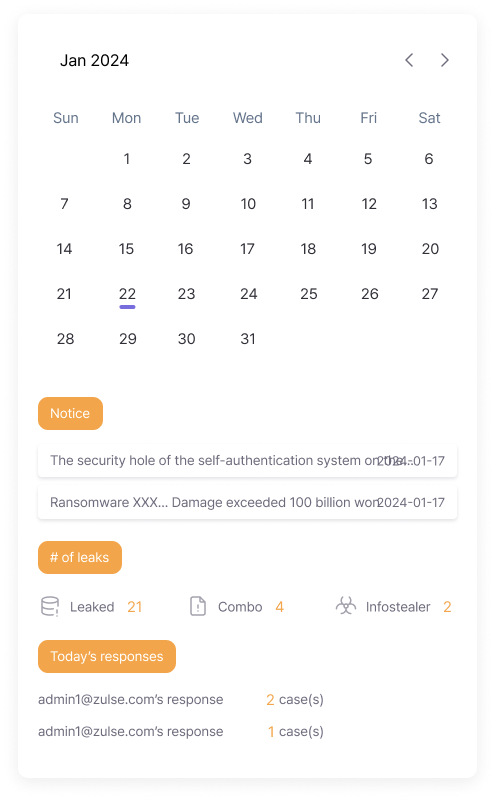
Dark Web Information Leakage Levels
Provides a detailed analysis of the severity of information leaks on the dark web, allowing companies to accurately assess the seriousness of security threats.

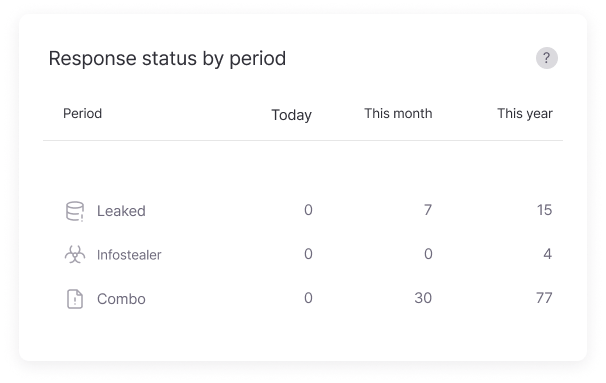
Response Status by Period
Provides the response status for information leaks by period, including daily, monthly, and cumulative totals, enabling users to track response activities over time.

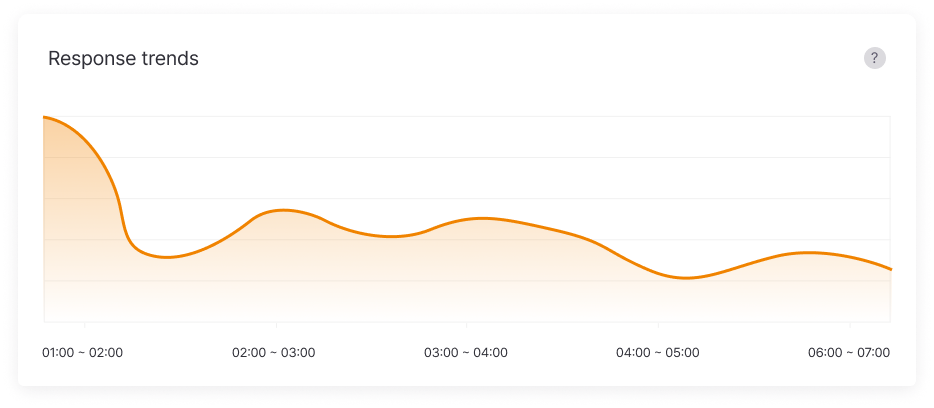
Leak Response Trends
Visualizes the trends in leak response activities, showing the effectiveness and progress of response actions.

Damage Increase/Decrease Trends
Visualizes the trends in damage increase/decrease related to leaks, showing the effectiveness and progress of response actions.

Detailed Leak Information
Provides detailed information on leaked accounts in a list view, with filtering and search functions to quickly locate specific information. The detailed view also offers leak history and recommended response actions.
Leakage Response History
The leakage response history feature allows companies to systematically manage and clearly track their response activities. By categorizing the response status by administrator account and date, companies can efficiently manage and analyze their response to leaks. This feature helps companies clearly understand the progress of response actions and continuously improve their cybersecurity posture.
Summary
Global Cyber Attacks
Domain Leak Report
Management
Leaked account
Response History
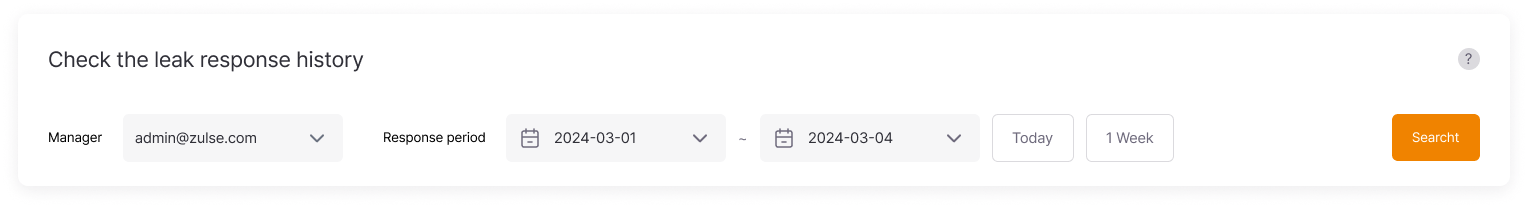
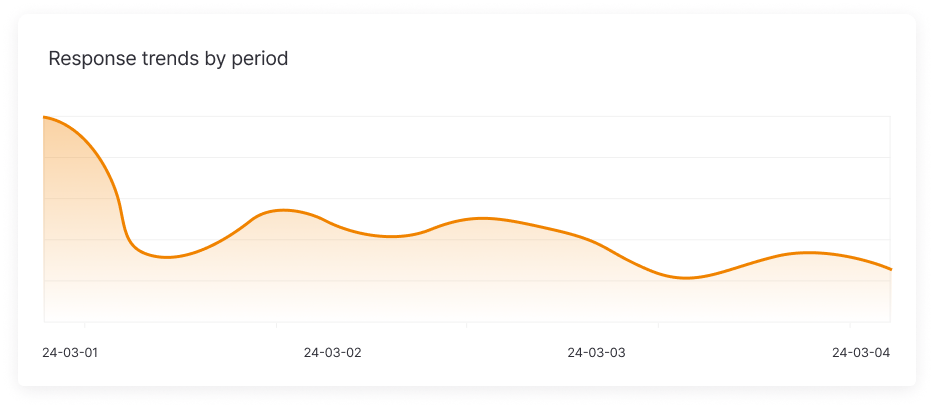


Leakage Response History Filtering
Filter response history by specifying the administrator and period, allowing users to manage and analyze response activities in more detail.

Response Trends by Period
Displays the trends in response activities over time in graph form, helping to visually assess response efficiency and identify areas for improvement.

Response Status
Provides the number of response actions by administrator, response period, and type, along with the totals, helping to clearly understand the details of each response activity.

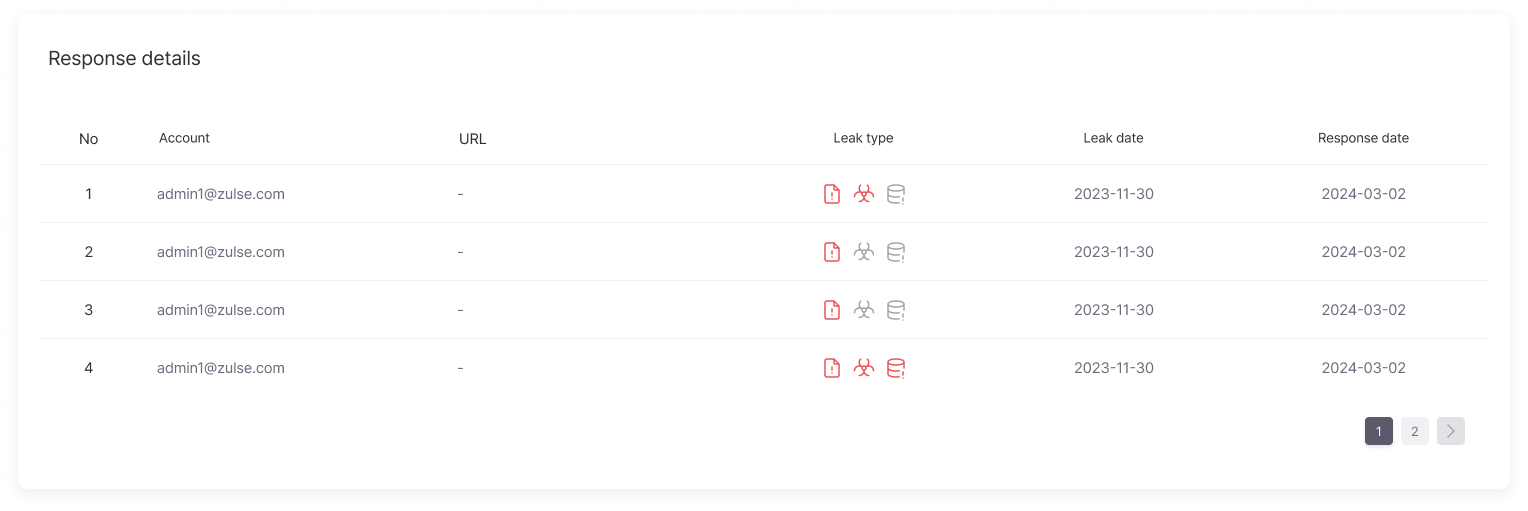
Detailed Response History
Provides detailed history for each response action, including ID, password, leak type, leak date, and response date, helping to understand the specifics of response activities.
Global Cyber Attack Trends
The global cyber attack trends feature aids companies in gaining a profound understanding of the global cybersecurity landscape. It identifies and highlights the top 20 countries most impacted by infostealers worldwide. The feature offers detailed analysis of the behavior patterns of cyber attack groups operating in specific countries of interest. Additionally, it provides information on the targeted sites, discovery dates, affected industries, and the extent of damage inflicted by these attack groups in other countries. This comprehensive information equips companies with the insights necessary to formulate strategies to counter global cyber threats effectively.
Summary
Global Cyber Attacks
Domain Leak Report
Management
Leaked account
Response History

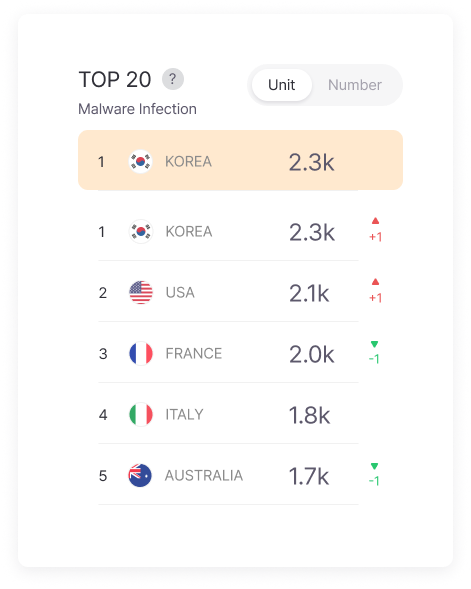

TOP 20 Infostealer-Infected Countries
Identifies and highlights the top 20 countries most impacted by infostealers worldwide. This information serves as a crucial basis for understanding the regions most active with cybersecurity threats.

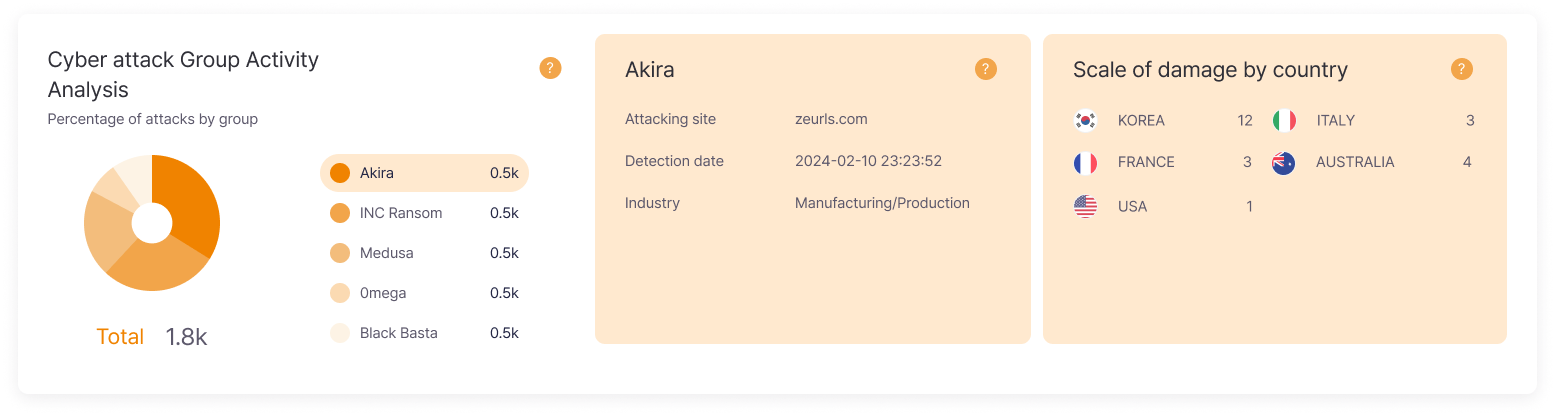
Attack Proportion by Group
Analyzes and displays the attack proportion by various cyber attack groups, helping to understand the activity patterns of specific groups and their preferred attack types.
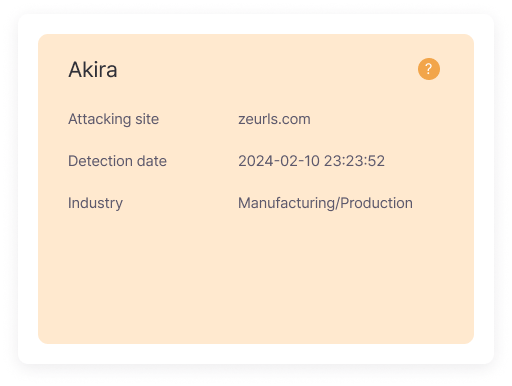
Group Attack Status
Provides detailed information on attacked sites, detection dates, and the affected industries. This data helps track the latest trends in cyber attacks and understand the threat levels faced by specific industries.
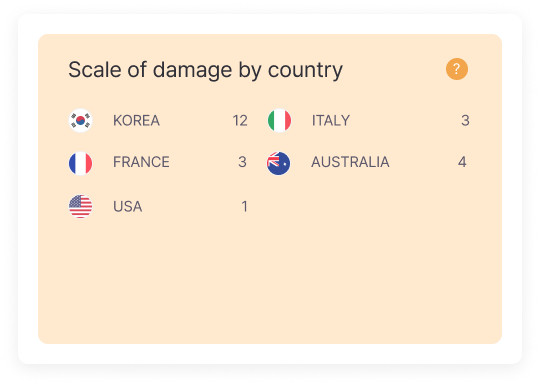
Damage Scale by Country
Shows the scale of damage each country has suffered from cyber attacks. This information is essential for evaluating how cyber threats are distributed globally and assessing the vulnerability of specific countries to cyber attacks.
ZeroDarkweb in numbers
Total Analyzed Data
221 B
Leaked Account Data
58 M
Leaks in the Sample Report
98.5 M
The Dark Web is the home ground of the ZeroDarkWeb.
You can address security issues with monitoring services without the need for a dark web specialist or advanced technical skills.

Monitoring
Designate domains to search for leaks on the dark web.

Email Leak Detection
Search for leaked email addresses and passwords.

Account Leak Detection
Search for leaked IDs, passwords, and access information.

Hacking Detection
Search for IPs suspected of being hacked.

Ransomware-Infected Device Detection
Continuously search for ransomware damage situations.
If you have similar concerns, try ZeroDarkWeb now.